Until Revit comes up with some kind of advanced and granular permissions management for workshared files, we are left with a situation that requires best-practice Revit use combined with 100% obedient staff. If you would like to take matters into your own hands in the meantime, you can use this somewhat scary hack to check out worksets using a concealed user name. As with many posts on What Revit Wants – use at your own risk!
In short:
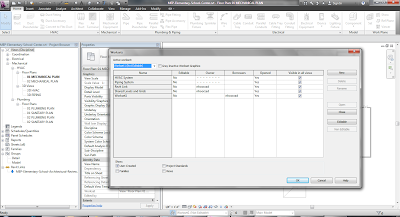
- Copy the username into Microsoft Word and change it to a different font in this example the font called AIGDT. (which is just associate symbols to letters).
- Copy the username (AIGDT font) back into Revit and as you can see Revit just shows it as bullets.
- Worksets checked out to that user will appear to others like this:
Image and idea by Navid at:
Locking WorkSet with a hidden user name!